
Addressing Cyber Kill Chain Framework
Addressing Cyber Kill Chain Framework
As per one of the reports published by Cyber Observer, “The average life cycle of a data breach is about 11 months”. Report also states that, it takes a total time of 314 days from the time of breach to successfully contain a cybersecurity attack. To be more factual, the average time taken to identify a breach is nearly about 7 months. Once identified it takes another 4 months to contain these breaches. The attacker deploys these malicious programs in stealth mode hence they appear as non-malicious in case of regular checkup making it very difficult to detect these programs.
As stated by Cybercrime Magazine “By the end of 2021, hacking will cost organizations about 6 trillion USD”. Hence it has become very important to have a foreknowledge of such attacks to prevent gigantic financial losses.
Once such way is to opt for a cyber kill chain model.
The “cyber kill chain” is a framework which depicts the sequence of stages which is required for an attacker to successfully infiltrate a network and extract data from it. Each stage of cyber kill chain demonstrates a specific goal along the attacker’s path which he chooses to follow.
Cyber Kill chain breaks the externally originating attacks into 7 different stages:
-
Reconnaissance
-
Weaponization
-
Delivery
-
Exploitation
-
Installation
-
CNC
-
Exfiltration
Step: 1
Reconnaissance - At the reconnaissance stage, the prime objective of the attacker is to gather information about the target organization. Tools used in the reconnaissance phase scans the corporate networks to search for entry points and vulnerabilities which can be exploited.
The reconnaissance is divided into 2 types:
In Passive reconnaissance a hacker looks for information not related to victim domain.
In Active reconnaissance a hacker uses system information to gain unauthorized access to protected materials, via routers or firewalls to get it.
For Example: Abnormal DNS reverse look up request
Step: 2
Weaponization: Based on what the attackers discovered in the reconnaissance phase, they’re able to infiltrate into the systems by leveraging the vulnerabilities found in the reconnaissance phase.
For Example: Brute Force Attack
Step: 3
Delivery: Once the attacker infiltrates into the system and the system is compromised, the attacker send malicious payload to the victim by means such as email, which is one of the multiple intrusion methods the attacker can use to compromise the System.
For Example: Adversary-released delivery, which conveys the malware to the target through phishing.
Step 4
Exploitation: Once delivered, the weapon’s code is triggered, and the malware starts the action. The program code of the malware is triggered explicitly to exploit the vulnerability/vulnerabilities of the compromised system.
Step 5
Installation: The malware installs a backdoor on a target’s system for the intruder/attacker giving them access to the target environment.
Step 6
Command-And-Control (CNC) - The attacker creates a command-and-control channel to continue to operate the compromised assets remotely. This step is relatively generic and relevant throughout the attack, not only when malware is installed.
Step 7
Exfiltration - It refers to how the attacker accomplishes his final goal. The attacker's final goal could be anything from extracting a ransom exchange for decrypting your files to exfiltrating customer information out of the network.
One of the most effective methods is to design the monitoring and the response plan around the Cyber Kill Chain framework as it focuses on how actual attack might happen in a sequenced way. To detect and mitigate each of the above-mentioned sequential phases, Zensar suggests a proven and well-defined approach as depicted in the diagram below.
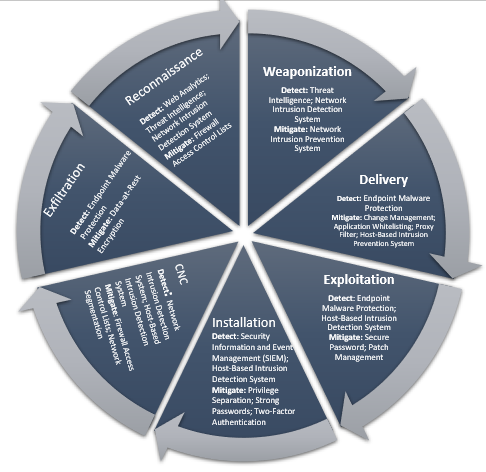
Zensar uses its robust SOC to offer near real time monitoring, detection and response to security incidents and intrusion attempts across a client’s Infra operations on a 24X7 basis. In a nutshell, our SOC plays a pivotal role in investigating, find the contextual information, and seek out unknown threats before the threat becomes real, instead of just relying upon threat detection system and alerts, which can be delayed. This is made possible through analysis of historic data combined with the hypothesis of previously undetected threats based on unique signatures of a newly identified malware strain or the TTP (Threat, Technique and Procedures) associated with the specific actor.



