
Trace out the Unknown with Microsoft Azure Sentinel – Threat Hunting
Read time: 5 Mins
Fighting asymmetric cyberbattles is the new normal for organizations of all sizes across all industries. Almost all organizations face attacks from a wide range of adversaries using tactics, techniques, and procedures that significantly differ from one another. The modern-day advanced cyber adversaries are typically highly skilled, well-funded, elusive, polymorphic, and bypass legacy security controls. These threat actors are undetected while in action because the anomalous attack pattern the attacker follows is unknown or evades the thresholds set in the detection rules.
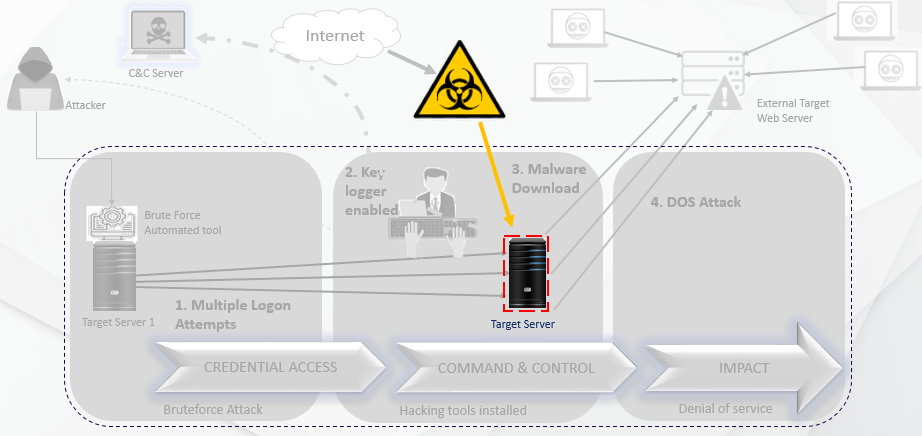
(a) Unknown Attack Pattern
When the attack pattern is undetected, and we must uncover the invisible dots to trace out the adversary, the Cyber Defense team needs to proceed with proactive threat hunting. As part of threat hunting, it is always observed that hunters usually start with a threat hunting hypothesis and hunt manually for IOCs, perform an anomaly based hunting, TTP based hunting, Network and Host based hunting from a large data set.
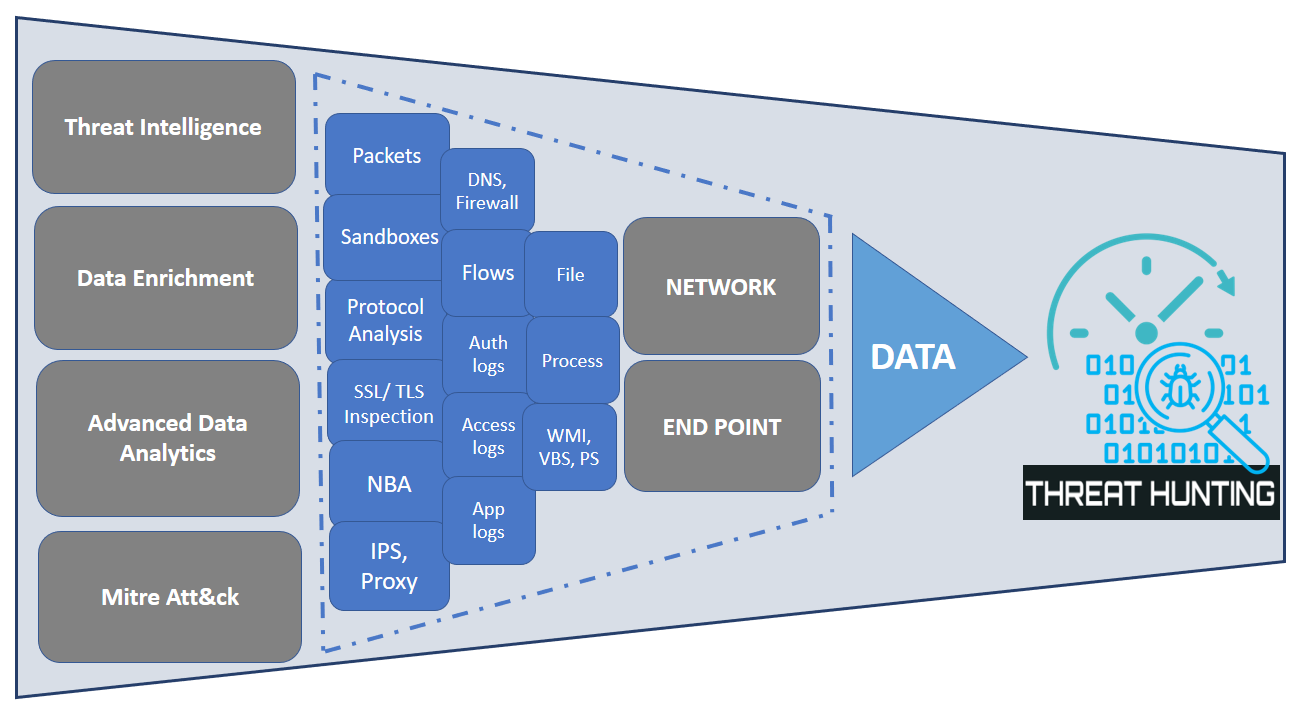
(b) Data sources for Hunting
A Threat Hunter’s Perspective
This traditional way of threat hunting does help an organization uncover undetected threats but are they entirely successful??
It’s a big NO because it is never enough, and there is always something more to consider where we fall short in time when it's threat hunting. Threat hunters perform a certain level of known investigation checks as part of their hunting based on the scenarios they consider, circling the mostly repetitive hypothesis. Azure Sentinel’s SOAR capabilities are the solution to such tasks, and leveraging the SOAR capability is the key which is not only for investigating an alert triggered by integration sources like SIEM or any other security control but also can act as source that performs Threat hunting.
The known investigation steps can be clubbed together based on the hunting scenario by enhancing the power of Mind maps. Mind maps is a structural way to perform the threat hunting to identify the unknown, unaccepted or malicious behavior in terabytes of data
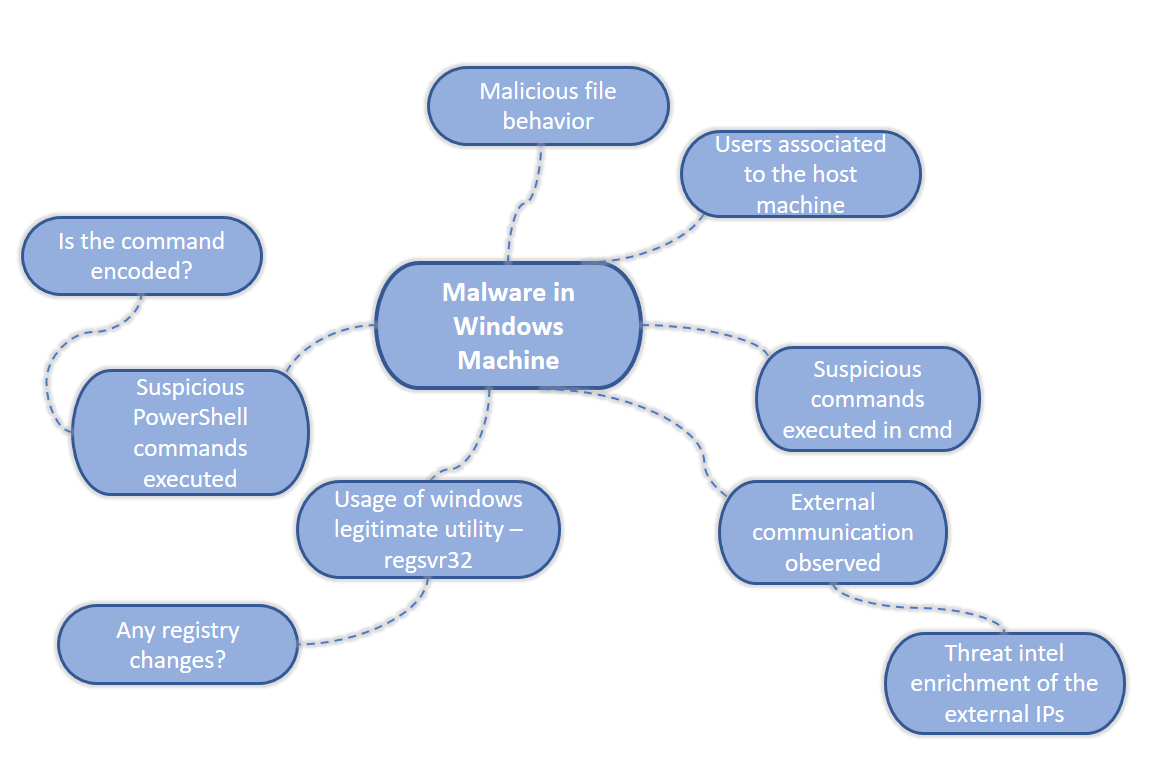
(c) Mind maps – Malware in windows hypothesis 1
Automated Threat Hunting – Mind maps driven approach with Azure Logic apps
The manual hunting process is time-consuming and requires ample amount of effort, which takes a few hours for a threat hunter to complete. Azure logic apps help automate most enrichment tasks for the hunting process and ease the response process for immediate containment/mitigation.
Multiple mind maps for all the threat hunting scenarios performed manually need to be charted down, further converted into automated hunting playbooks using Azure logic apps. These playbooks generate a final detailed threat hunting report specific to each mind maps driven scenario which are shared across over email and gives a complete visibility to the threat hunter or a SOC manager to decide on the response action. The SOC manager is given the flexibility to take an action immediately from the same email notification received which is just a click away, to block any communication to the external entity observed from the infected host machine.
This automated threat hunting approach does not aim to eliminate manual threat hunting but to improve the Threat hunting process where the hunter can invest time on performing unique investigations manually rather than the known repetitive tasks.
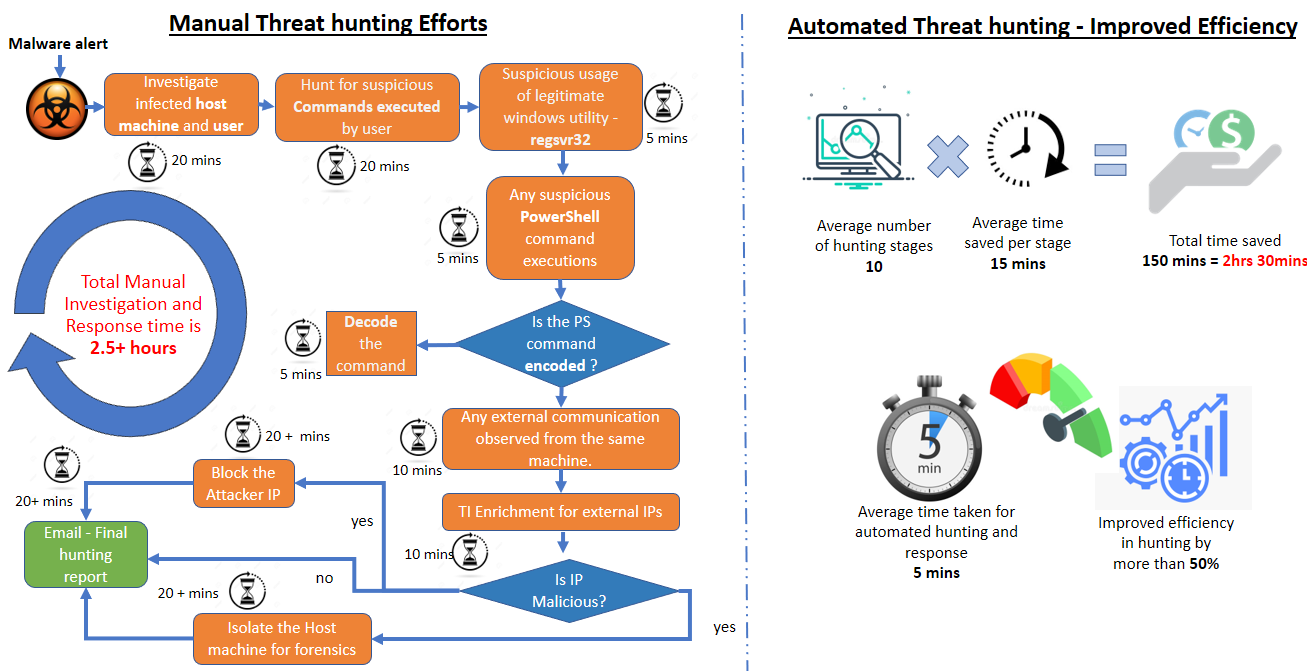
(d) Automated Threat Hunting – Improved efficiency
The skeleton of an automated threat hunting playbook with a detailed explanation of the logic apps' steps will be available in part 2 of this blog series. Stay Tuned…!!



