Identity and Access Management
Identity and Access Management
We follow the do not trust - always validate principle, focusing on user identity authentication, ensuring least privilege, enabling conditional access-driven solutions, and adhering to regulatory compliance.

Identity and Access Management

We follow the do not trust - always validate principle, focusing on user identity authentication, ensuring least privilege, enabling conditional access-driven solutions, and adhering to regulatory compliance.
Why is identity and access management so important?
Achieve operational excellence with Zero Trust Model
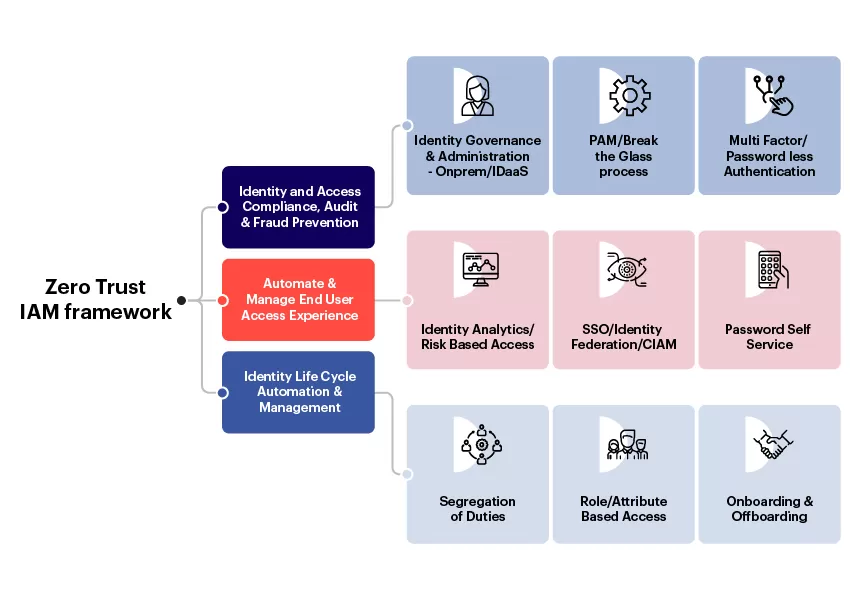
Our Capabilities
Digital Security Offerings
Our experience
Explore other offerings

Hybrid Cloud Services
Build a technology foundation to move data, hyper-connect user devices, and run workloads with unparalleled availability and scale.
Take me there
Intelligent Hybrid Infrastructure Services
Drive operational efficiency with human smarts backed by machine intelligence
Take me there






